Computing Cluster Terms of Use
Version 1.1 5-11-2022
The Benefit Advanced AI and Computing Lab was kindly donated by Benefit Bahrain Company for the use of researchers and students at the College of Information Technology, University of Bahrain. The main aim of this computing facility is to provide cutting edge computing infrastructure for learning and research in AI and HPC. The cluster is intended as a small efficient cluster for learning/testing new technologies and not a production level server.
The following document contains the terms of use that will ensure the secure and fair use of this important resource by all users.
privileges.
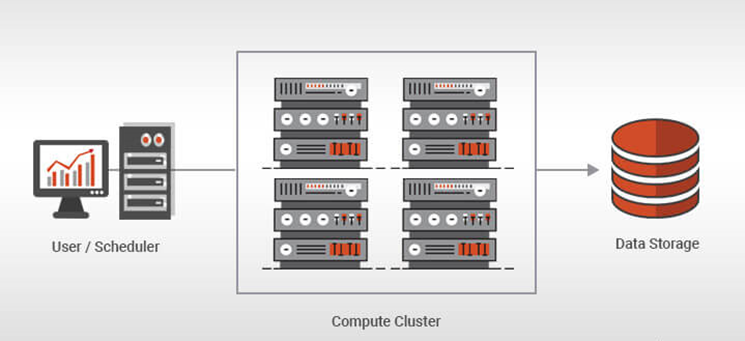
Figure 1. Benefit Advanced AI Lab Cluster Architecture
Computing Cluster Use
- Accounts on the Benefit Advanced AI and Computing cluster are available to UOB faculty, staff, and students who conduct research. A faculty member must sponsor student accounts. External researchers can use the resources as long as they are sponsored by a PI staff member from the College of IT.
- The Benefit Advanced AI Lab Committee maintains current documentation and support, provides regular training on the use of the cluster. Users assume the responsibility for following the documentation, training sessions and best practice guides in order to understand the proper and considerate use of the cluster’s computing resources.
- The computing resources of the lab are maintained by a scheduler and queuing system called the Slurm workload manager. This scheduler implements rules based on fair sharing principles.
- Large scale experiments involving either large individual jobs or many smaller jobs launched in rapid succession must be done with the guidance and prior approval of the administrators of the lab. Users should allow the workload manager to generate optimal job schedules by providing wall time and proper requirements. Computational tasks that impact the functioning of the platform or the user experience may be terminated, and the user notified.
- Users must comply with resource limits as defined in the queueing system and/or communicated by the Benefit AI Lab Committee.
- Users are prohibited from running applications for personal gain on cluster resources such as applications that mine cryptocurrency. Users repeatedly violating these policies may be denied access to cluster facilities.
- Users must not intentionally introduce or use malicious software on Benefit AI Lab facilities, including but not limited to viruses, worms, ransomware, etc.
Data and Storage Use
- Use of Benefit AI data storage resources (file systems, data storage tiers, backup, etc.) should be used only for work directly related to the projects for which the resources were requested and granted, and primarily to advance University’s missions of education, research, and service. Use of data and storage resources for personal activities is prohibited.
- Owners of information or data are responsible for its correct categorization as sensitive or non-sensitive. Owners of sensitive information are responsible for its secure handling, transmission, processing, storage, and disposal on the Benefit AI Lab systems. Users are advised to use encryption and to maintain backups of any critical data.
- Users are prohibited from intentionally accessing, modifying or deleting data they do not own or have not been granted explicit permission to access.
- In the event of system failure or malicious actions, the Benefit AI Lab makes no guarantee against loss of data or that user or project data can be recovered nor that it cannot be accessed, changed, or deleted by another individual.
User Responsibilities
- Users are only allowed one account per person.
- Sharing of user credentials (including but not limited to the User Account password, Private keys and their passphrases) is strictly prohibited.
- Users are provided with a strong password for their Account when it is created. When changing this password, users must choose a strong password that should be unique to their Benefit AI Lab User Account.
15. Users should inform the Benefit Lab Team promptly of any changes in their contact information (email, affiliation, etc.). - Users must never try to circumvent login procedures on any Benefit AI Lab resource or otherwise attempt to gain access where they are not allowed.
- Users must never deliberately scan or probe any information resource without prior authorization.
Publication and Crediting the Benefit Advanced AI Lab
- Users agree to ensure that all publications or other outputs, which involved the use of Benefit AI Lab resources credit them appropriately as described below.
- Users agree to provide on request reports detailing their Users’ accomplishments achieved with involvement of Benefit AI Lab resources and expertise.
- Citing the Benefit Advanced AI and Computing Lab in an acknowledgment section of a publication
Acknowledgment: The experiments presented in this paper were carried out using the facilities of the Benefit Advanced AI and Computing Lab at the University of Bahrain {small — see url{https://ailab.uob.edu.bh}} with support from Benefit Bahrain Company {small — see url{https://benefit.bh}}.
User Account Request Form
Usage Policies
By submitting this form, users agree to the following policies:
- Use the batch submission system of the scheduler (SLURM).
- Users may not run applications interactively from the login node.
- Users may not log into the compute nodes for the purpose of running a job directly without permission from the Benefit AI Lab committee.
To request access other than batch submission, please send a request explaining why special access is necessary for your research to ailab@uob.edu.bh . - Unauthorized Interactive jobs or applications found running on the login node(s) or on the compute nodes outside of Benefit AI Lab are subject to immediate termination.
- Respond in a timely way to correspondence from the Benefit AI Lab Committee.
All correspondence will be sent to the e-mail address on file with the Benefit AI Lab committee. - Users must not attempt to access other users’ data or install unauthorized or malicious software on the cluster.
- Comply to the detailed Benefit Computing Cluster Terms of Use.